A single SIP server failure can turn a safety phone into a silent box. In a hazardous area, that risk feels unacceptable during an incident.
Yes. Dual SIP on an explosion-proof telephone 1 can provide redundancy when each account is mapped to a different server or network path, and failover rules are tuned for fast detection and stable failback.
Dual SIP redundancy is real, but it is not automatic by default
Dual SIP can mean four different redundancy modes
Many buyers hear “dual SIP” and assume automatic hot-standby. …Some devices do that. …Many devices do not. Dual SIP 2 usually supports two independent registrations, but the failover behavior depends on firmware logic and PBX policy.
These are the common modes seen in the field:
-
Hot-standby: Line 1 is active. …Line 2 stays registered and takes over when Line 1 fails.
-
Active-active: Both lines stay registered and can ring at the same time. Outbound calls choose a preferred line.
-
Service split: Line 1 is normal calling. Line 2 is emergency calling and paging only.
-
Manual fallback: Line 2 is available, but it needs a user action or a reboot to switch.
A design should pick one mode and document it. Mixing modes creates confusion during drills.
Failure detection is the real “redundancy engine”
Failover is only as fast as failure detection. A phone that waits for a 30–60 second registration timeout can feel “down” for a long time. A phone that checks reachability every few seconds can fail over quickly, but it can also flap when the network is jittery.
The most reliable pattern is:
-
Keep both accounts registered.
-
Use keepalives (OPTIONS, CRLF, or similar) to detect loss fast.
-
Add a short hold time before failback to stop ping-pong behavior.
-
Keep emergency routing separate so a server failure does not block the alarm path.
The most common traps
Redundancy projects usually fail for one of these reasons:
-
Both SIP accounts point to the same IP or same upstream switch.
-
DNS SRV exists, but the phone caches the old record for too long.
-
Keepalives are disabled, so failover waits for expiry timers.
-
The PBX accepts the registration, but routing rules send calls to a dead trunk.
-
TLS handshake and certificate checks slow re-registration under stress.
| Item | What it controls | Good redundancy behavior | Typical failure |
|---|---|---|---|
| Two SIP accounts | Two independent registrations | Separate servers and paths | Same server, no real backup |
| Keepalive method | Fast detection | Detects loss in seconds | Waits for long timeouts |
| Failback hold time | Stability | Prevents flapping | Switches back and forth |
| PBX routing | Where calls go | Emergency routes stay available | Calls still hit dead trunk |
| Network path | Physical resilience | Separate uplinks/VLANs | One switch takes both down |
A simple rule helps: redundancy should be proven with a real failure test. Pull the primary server link. Confirm the call and SOS workflows still complete. Then restore and confirm clean failback.
The next step is to decide if two SIP accounts can do true hot-standby in your environment.
Can two SIP accounts register to primary and secondary servers for hot-standby failover?
A phone can show two “registered” lines and still fail under pressure. Hot-standby needs more than two green status icons.
Two SIP accounts can register to primary and secondary servers for hot-standby 3 failover when the phone supports automatic line preference switching, and the PBX treats both registrations as valid emergency endpoints.
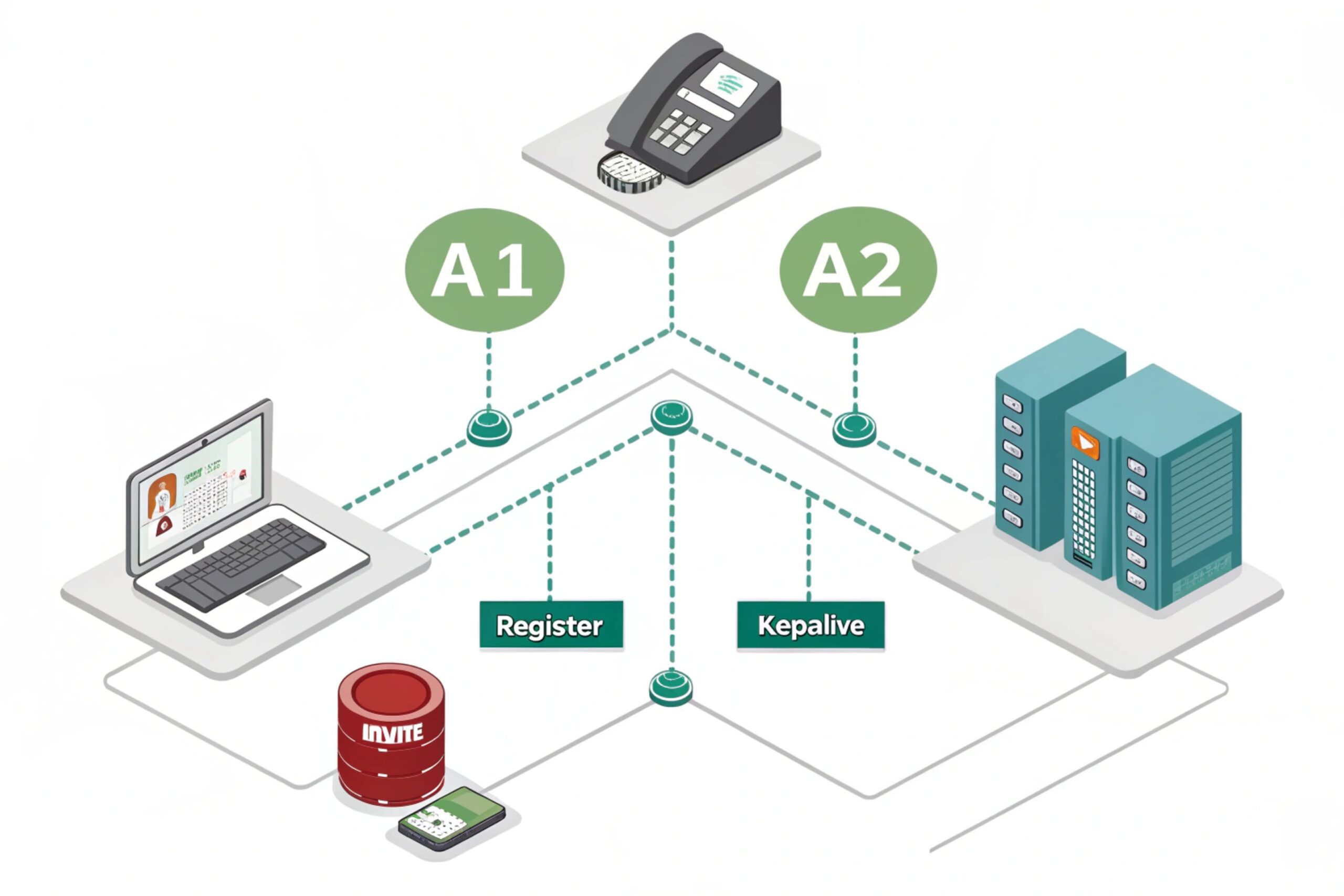
Hot-standby works best when one line is “preferred” and the other is “ready”
True hot-standby has three required parts:
1) Preferred outbound line: the phone uses Line 1 by default for calls and signaling.
2) Parallel registration: Line 2 stays registered to the secondary server all the time.
3) Automatic promotion: the phone promotes Line 2 when Line 1 is unreachable.
If a phone only registers Line 2 after Line 1 fails, the failover time becomes longer. That is still redundancy, but not hot-standby.
A stable design also uses different DNS names and different IP ranges for the two servers. That reduces shared failure modes.
PBX-side design matters as much as phone-side design
Even with perfect phone failover, the PBX must still route calls correctly:
-
Inbound calls to the phone should ring on both registrations or on the active one, based on your policy.
-
Emergency calls from the phone should always reach the dispatch group, even if one PBX node is down.
-
Paging and priority override should be consistent for both accounts.
Some sites use two PBXs (primary and backup). Others use one clustered PBX with multiple nodes. Both can work, but the phone should not depend on a single IP element.
What to configure for predictable behavior
A hot-standby setup usually needs:
-
A clear “line preference” order for outbound calls.
-
A clear rule for which line is used for SOS or emergency button action.
-
A clear rule for how inbound calls ring (ring both, ring primary only, or ring whichever is active).
-
A clear log and LED behavior so technicians can see which line is active.
| Setting | Recommended choice for hot-standby | Why it helps |
|---|---|---|
| Outbound default line | Line 1 (primary) | Keeps normal calling stable |
| Emergency action line | Line 2 (backup) or “best available” | Keeps SOS alive when primary fails |
| Registration state | Keep both registered | Cuts failover time |
| Inbound ringing | Ring both if policy allows | Improves reachability |
| Failback behavior | Delay failback by a hold timer | Stops frequent switching |
In my deployments, the cleanest hot-standby design uses Line 1 for normal calls and Line 2 reserved for emergency workflows. That separation reduces arguments during audits. It also simplifies tests.
Next comes the transport layer features that make switchover automatic without manual intervention.
Do DNS SRV records, outbound proxy, and SIP keepalives enable automatic switchover and graceful failback?
A failover plan that depends on humans rebooting phones will fail during a real event. Automatic switchover needs the phone to detect loss and find the next target fast.
DNS SRV, outbound proxy settings, and SIP keepalives can enable automatic switchover and graceful failback when DNS caching is controlled, keepalive intervals are tuned, and the phone uses a stable priority order with a short failback delay.
DNS SRV: useful, but only when TTL and caching are respected
DNS SRV 4 gives a prioritized list of targets. That helps phones discover multiple servers without hardcoding IPs. It also supports weighting for load sharing.
In practice, DNS SRV works well when:
-
Records are configured with clear priorities for primary and secondary.
-
DNS TTL is set to a value that matches failover expectations.
-
Phones and SBCs do not cache records longer than intended.
A problem appears when a device holds the old SRV answer for minutes after the primary fails. That makes redundancy feel broken even though SRV exists.
Outbound proxy: the simplest “one target” method
An outbound proxy 5 (often an SBC or a proxy pair) is a strong pattern for industrial sites:
-
Phones always register to the proxy.
-
The proxy decides which PBX node is active.
-
The proxy can handle NAT, TLS, and policy consistently.
This reduces complexity at the endpoint. It also centralizes troubleshooting. Many sites prefer this because the hazardous area devices stay simple.
Keepalives: the difference between fast failover and slow failover
Registration expiry is not a fast detector. Keepalives are. Common keepalive methods include:
-
SIP OPTIONS “qualify”
-
…CRLF keepalive
-
Re-INVITE/session refresh checks (less ideal as a detector)
A practical strategy is:
-
Use SIP keepalives 6 every 15–30 seconds for critical emergency phones.
-
Use a failure threshold (for example, a few missed keepalives) to trigger switchover.
-
Add a failback hold time so restored links do not cause flapping.
| Tool | What it solves | Best practice | What to avoid |
|---|---|---|---|
| DNS SRV | Target discovery and priority | Set clear priorities and sane TTL | Long caching that blocks failover |
| Outbound proxy | Central policy and HA | Use proxy pair with health checks | Single proxy as new single point |
| Keepalives | Fast failure detection | Short interval + missed count | Relying only on reg expiry |
| Failback delay | Stability | Add hold timer | Immediate failback ping-pong |
A graceful failback should feel boring: the phone stays on backup until the primary is stable for a while. Then it returns without dropping active calls where possible. That behavior must be tested, not assumed.
Next is network isolation. Many plants want emergency voice isolated from normal voice, or isolated from CCTV traffic.
Can each SIP line use separate VLANs or dual LAN ports to isolate voice and emergency services?
A single flooded VLAN can break voice at the worst time. A single uplink failure can also remove both “redundant” SIP lines if they share the same path.
Yes. Each SIP line can use separate VLANs or dual LAN ports when the hardware supports interface binding and the network design provides truly separate upstream paths, so emergency services stay available during congestion or partial failures.
VLAN separation: the common and clean method
VLAN 7 separation is practical because it uses the same physical port but different logical networks:
-
VLAN A for normal voice and office services
-
VLAN B for emergency voice and critical paging
-
Separate QoS policies and rate limits for each VLAN
VLAN separation works best when the upstream switch and core routing enforce:
-
strict QoS marking and trust boundaries
-
multicast control if paging uses multicast
-
bandwidth protections so video traffic cannot starve voice
A limit exists: one physical link is still one physical link. A cable cut or a switch port failure still takes both VLANs down.
Dual LAN ports: stronger physical resilience when done right
Some rugged devices offer dual LAN ports or dual-homing features. In redundancy design, dual LAN can mean:
-
one port to Switch A, one port to Switch B
-
separate power domains if PoE switches are separate
-
separate VLANs on each port for clean isolation
Dual LAN only provides real redundancy if the upstream paths are independent. If both ports land on the same switch stack with one uplink, redundancy is weaker than it looks.
Mapping SIP lines to network interfaces
The best outcome happens when:
-
Line 1 uses Interface A and registers to PBX A
-
Line 2 uses Interface B and registers to PBX B
-
Emergency button uses the interface and line that stays alive during the most likely failure
Some devices cannot bind a SIP account to a specific interface. In that case, VLAN priority and routing rules must do the work.
| Network method | What it protects against | What it does not protect against | Best use |
|---|---|---|---|
| Separate VLANs on one port | Congestion and broadcast control | Cable/port failure | Most plants with good switching |
| Dual LAN to two switches | Port and switch failure | Core outage if both depend on one core | Critical emergency stations |
| Separate PoE switches | Local power loss | Phone internal failure | High-availability design |
| Emergency-only VLAN | Traffic isolation | Misconfiguration risk | Sites with strict OT governance |
In harsh plants, isolation is often worth more than raw codec quality. A stable emergency VLAN with strict QoS can keep speech clear even when CCTV traffic spikes.
Next is the tuning detail that decides whether failover is fast, stable, and secure under real SIP stacks.
How do TLS/SRTP, timers, and re-registration settings affect failover reliability with Asterisk, 3CX, and CUCM?
Security and redundancy often fight each other if timers are poorly tuned. Fast failover needs fast detection and fast re-registration. TLS adds handshakes and certificate checks.
TLS/SRTP, SIP timers, and re-registration settings strongly affect failover reliability because they control handshake time, failure detection speed, and how quickly endpoints move between servers. Good results come from short keepalive intervals, sane registration expiry, stable session timers, and consistent policies on Asterisk, 3CX, and CUCM.
TLS and SRTP: secure is good, but handshake timing must be planned
TLS protects signaling. …SRTP protects media. These are valuable in industrial networks, especially when voice shares infrastructure with other systems. Still, TLS/SRTP 8 can slow down:
-
initial registration
-
re-registration during failover
-
reconnect after a link flap
This does not mean TLS is a bad idea. It means the design should:
-
keep certificate chains clean and trusted
-
avoid frequent renegotiation
-
use stable server names (FQDN) that match certificates
-
keep time sync solid, because bad time breaks certificate validation
SRTP also adds overhead, but it is usually not the limiting factor. Network jitter and buffer behavior are bigger drivers.
Timers: the “hidden steering wheel” of failover
These settings often decide success:
-
Registration expiry: long expiry reduces traffic but slows “natural” recovery.
-
Re-registration interval: too frequent can overload servers during storms.
-
Keepalive frequency: controls failure detection speed.
-
Session timers: affect call refresh behavior on long calls.
-
DNS refresh behavior: controls how fast SRV changes are used.
A robust emergency setup uses short keepalives and moderate registration expiry 9. It also uses a failback delay so the phone does not bounce during brief primary recovery.
PBX notes without vendor-specific promises
Asterisk, 3CX, and CUCM can all support resilient designs, but each one has its own knobs and defaults. The safe plan is to align on principles:
-
Keep endpoints and servers aligned on codec and security policies.
-
Use health checks (OPTIONS/qualify) on both sides where possible.
-
Keep routing objects (queues, hunt groups) stable so failover does not change who answers.
-
Test failover under load, not only in a quiet lab.
Asterisk environments often succeed when endpoint reachability checks are enabled and the system can quickly mark an endpoint unreachable. 3CX environments often succeed when FQDN-based design and SBC patterns are used cleanly. CUCM environments often succeed when redundancy is built into the call control cluster and phone registration targets are designed for failover behavior.
A practical timer profile that is easy to explain
| Area | Goal | Recommended approach | Why it helps |
|---|---|---|---|
| Keepalives | Fast detection | 15–30 seconds, few misses to declare down | Failover in seconds, not minutes |
| Registration expiry | Stability | Moderate expiry, avoid extreme values | Reduces churn and overload |
| Re-registration | Predictable recovery | Use jittered retries and backoff | Prevents storms after outage |
| TLS validation | Prevent failures | NTP sync + correct FQDN and cert chain | Stops random “untrusted” errors |
| Failback | No flapping | Hold time before returning to primary | Keeps calls stable |
In my field acceptance tests, the most revealing step is simple: pull the primary PBX link while a normal call is active, then press SOS on another station. The design passes only when SOS still reaches dispatch and the system logs the event with correct time and device ID.
Conclusion
Dual SIP redundancy works when accounts, network paths, and timers are designed as one system. Keep failover fast, keep failback stable, and keep emergency services isolated and tested.
Footnotes
-
Hazardous area communication device designed to contain sparks and withstand harsh industrial conditions. [↩] ↩
-
Configuration using two active SIP registrations to ensure continuous service availability during server failures. [↩] ↩
-
Redundancy method where a backup system immediately takes over processing upon primary system failure. [↩] ↩
-
DNS records specifying the hostname and port for specific services like SIP to facilitate load balancing. [↩] ↩
-
Intermediary server that routes SIP requests to their destination, handling NAT and security policies. [↩] ↩
-
Mechanisms like SIP OPTIONS or CRLF used to verify connection status and maintain NAT bindings. [↩] ↩
-
Logical network segmentation separating voice traffic to ensure Quality of Service and security. [↩] ↩
-
Security protocols encrypting SIP signaling (TLS) and media streams (SRTP) to prevent eavesdropping. [↩] ↩
-
Time duration a SIP registration remains valid before requiring renewal to maintain connectivity. [↩] ↩











