A phone can look online while it is already unreachable. In hazardous areas, that false sense of safety can delay help when a real call must go through.
Yes. Most explosion-proof SIP telephones can support heartbeat monitoring using SIP keepalives, registration refresh, transport keepalives, and optional NAT tools. A good design also exposes health to NMS and triggers failover actions when the heartbeat fails.

A practical heartbeat design for explosion-proof VoIP phones
Heartbeat monitoring is not one feature. It is a design pattern. It has three layers: the network link, the SIP control plane, and the media plane. Each layer can fail in a different way. A plant also needs different reactions for each failure. A short SIP flap should not trigger a loud local alarm. A long loss of registration should.
In many industrial plants, the first cause of “offline” is not the phone. The cause is an access switch reboot, a PoE brownout, a fiber uplink issue, or an OT firewall rule change. A good heartbeat design checks more than one signal so the NMS does not cry wolf.
A clean pattern uses:
- Layer 1/2: link status and PoE status from the switch, plus device uptime.
- Layer 3/4: transport reachability (TCP keepalive for TCP/TLS) or NAT binding stability for UDP.
- Layer 7: SIP reachability and registration state (OPTIONS and REGISTER).
- Call quality: RTCP quality and packet loss, when available.
Heartbeat also needs timing rules. A short interval gives fast detection. It also increases traffic and false alarms during congestion. A longer interval reduces noise, but it delays response. The best result uses two clocks: a fast local keepalive for NAT and SIP reachability, and a slower NMS alarm timer with hysteresis.
Here is the model that works well for large deployments:
Use multiple signals, then alarm only on confirmed failure
One failed ping should not mean “offline.” A plant should define “offline” as a set of failures over time. The phone should also log the reason, because “lost SIP” and “lost Ethernet link” are different problems.
Define what “healthy” means for the site
A phone can be registered but still fail calls if RTP is blocked. A phone can pass RTP but fail incoming calls if registration expired. Health should include: registered, reachable, and able to place a test call route (if the platform supports it).
| Health layer | Best signal | What it detects | What it misses |
|---|---|---|---|
| Link and power | Switch link + PoE + phone uptime | Cable pull, PoE limit, reboot | SIP server failure |
| SIP reachability | SIP OPTIONS 1 | Proxy reachability, routing issues | Media path problems |
| Registration state | REGISTER refresh status | Account and auth state | Short path issues between refreshes |
| Transport state | TCP keepalive 2 | Broken TCP sessions | UDP NAT expiry |
| Media quality | RTCP 3 stats | Jitter and packet loss | “No SIP” failures |
This pattern makes the next sections easier. Each section is one building block: keepalive methods, timing rules, platform integration, and failover actions.
A good heartbeat should not only detect failure. It should also point to the fastest fix.
Which keepalive methods are supported—SIP OPTIONS, REGISTER refresh, TCP keepalive, or STUN/NAT traversal?
A single keepalive method rarely fits every plant. Some sites use UDP. Some use TCP/TLS. Some have NAT. Some have no NAT and still have noisy switches.
The most common and reliable mix is SIP OPTIONS for fast reachability, REGISTER refresh for account state, and TCP keepalive for TCP/TLS transports. STUN and NAT traversal tools matter mainly when the phone sits behind NAT and uses UDP.
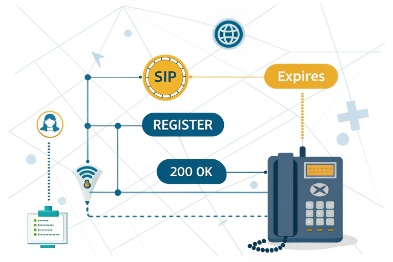
SIP OPTIONS: fast reachability without re-registering
SIP OPTIONS works like a lightweight “are you there” check to the proxy or peer. It is useful because it detects a broken path even when the registration has not expired yet. It also gives a clean state change that many platforms can display.
A good OPTIONS design uses clear rules:
- Send OPTIONS to the active proxy.
- Treat a short burst of missed replies as “degraded,” not “offline.”
- Switch proxy only after multiple misses.
REGISTER refresh: proves identity and inbound routing
SIP REGISTER 4 refresh tells the platform that the phone is still present and still allowed to receive calls. It also keeps NAT bindings alive when the phone uses UDP, if the refresh is frequent enough.
REGISTER is not a good fast heartbeat by itself. Many deployments use long registration expiry values. That helps reduce load. It also means failure can take minutes to show if REGISTER is the only signal.
TCP keepalive and SIP over TCP/TLS: stable sessions, but still need timers
When a phone uses SIP over TCP or TLS, the session can look alive even after the path breaks, because the break is not always detected immediately. TCP keepalive helps detect dead connections. Many platforms also support SIP outbound style flow keepalives or application-level CRLF keepalive, which keeps NAT bindings and detects broken sockets faster than OS-level TCP keepalive alone.
STUN and NAT traversal: useful only when NAT is real
STUN 5 is a NAT discovery tool. It helps endpoints learn public mapping details. In a plant LAN with no NAT, STUN adds little. In remote sites with NAT, STUN helps maintain UDP bindings and supports better media path selection when the SIP server is outside.
A practical selection table helps procurement and deployment teams:
| Method | Works best with | Primary value | Risk if misused |
|---|---|---|---|
| SIP OPTIONS | UDP or TCP/TLS | Fast proxy reachability check | Too frequent checks create load |
| REGISTER refresh | All transports | Keeps inbound routing alive | Long expiry delays failure detection |
| TCP keepalive | TCP/TLS | Detects dead sockets | Default OS timers can be too slow |
| STUN | UDP behind NAT | Helps NAT traversal and mapping | Adds complexity in no-NAT plants |
In my deployments, the most stable design uses OPTIONS as the “fast pulse” and REGISTER as the “identity anchor.” TCP keepalive sits under both when TCP/TLS is used.
The next step is to set timing rules that do not generate false alarms in NMS or SCADA.
How should heartbeat interval, timeout, and retries be set to avoid false offline alarms in NMS/SCADA?
A plant network is not a quiet office LAN. Switches reboot. Links flap during maintenance. Congestion spikes during camera bursts. A heartbeat must tolerate that reality.
Set device keepalives fast enough to keep sessions and NAT stable, then set NMS alarms slower with hysteresis. A common pattern uses 20–60s keepalive intervals, 2–4s timeouts, 2–3 retries, and a “3 of 5 failures” rule before raising an offline alarm.
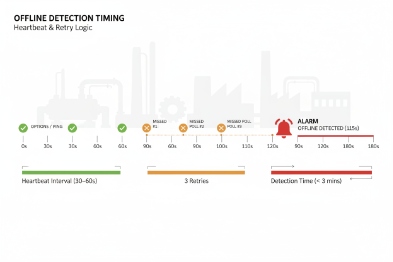
Use two timing layers: device timers and monitoring timers
Device timers are for session stability. Monitoring timers are for alarm stability. These two goals conflict, so they should not share one number.
- Device layer: keep NAT bindings alive and detect proxy loss quickly.
- Monitoring layer: confirm failure before alarming operators.
A simple, stable starting configuration
These starting points work well for many industrial LAN designs:
- SIP OPTIONS interval: 30 seconds (20 seconds if NAT is strict).
- OPTIONS timeout: 3 seconds.
- OPTIONS retries: 2 (so one missed reply does not flip state).
- REGISTER expiry: 300–600 seconds (site-dependent).
- TCP keepalive (if TCP/TLS): enable and use an application keepalive if available.
For the NMS/SCADA side:
- Poll or evaluate health every 60 seconds.
- Raise “degraded” after 2 consecutive failures.
- Raise “offline” after 3–5 minutes of confirmed failure.
- Clear alarm only after 2 consecutive successes.
Add jitter tolerance and maintenance awareness
A monitoring platform should also ignore short gaps during known maintenance windows. Many plants already have a change window. The monitoring rules should match that window.
A good alarm design distinguishes “phone unreachable” from “SIP not registered.” The first is often cabling, PoE, or switch. The second is often server, auth, or VLAN routing.
| Site condition | OPTIONS interval | Timeout | Retries | NMS offline rule |
|---|---|---|---|---|
| Clean LAN, no NAT | 60s | 3s | 2 | 3 failures over 3–5 minutes |
| Industrial LAN, bursty traffic | 30s | 3–4s | 2–3 | 5 failures over 5 minutes |
| Remote site with NAT | 20–30s | 3s | 2 | 3 failures + NAT/transport check |
| High-latency links | 60s | 5s | 3 | 3 failures over 6–10 minutes |
Use “reason codes” to prevent wrong dispatch
When the phone reports a state change, the platform should record the reason:
- Link down
- DHCP failure
- SIP auth failure
- Proxy unreachable
- RTP quality degraded
This makes alarms actionable. It also reduces repeat truck rolls.
Once timing is stable, the next question is integration. A plant does not want to check five dashboards. Health should flow into the platform the site already uses.
Can health status integrate via SNMP traps, HTTPS webhooks, or MQTT with third-party monitoring platforms?
If monitoring is slow or fragmented, alarms are ignored. A good integration pushes health to the tools that the plant already trusts.
Yes. Many industrial SIP phones can integrate health status through SNMP (polling and traps). Some platforms also support HTTPS callbacks or webhook-style event pushes. MQTT is a strong fit when the plant already uses an OT message bus for alarms and telemetry.

SNMP: the default for industrial NMS
SNMP 6 works well because switches, firewalls, and endpoints can share one monitoring model. Polling works for steady-state metrics. Traps work for fast events. For hazardous-area phones, useful SNMP points include:
- Registration state (registered/unregistered)
- Network status (IP address, link state)
- Device uptime and reboot reason
- Temperature alarm (if supported)
- Relay and input status (if present)
Traps reduce detection time. Polling confirms trends.
HTTPS webhooks: simple integration with modern platforms
Webhooks 7 are useful when the monitoring platform is cloud-friendly or when the site wants direct event push into an incident system. A phone or management server can post events like:
- “SIP offline”
- “Recovered”
- “Tamper”
- “Call placed to emergency number”
HTTPS also supports mutual authentication and certificates when the site has a PKI policy.
MQTT: strong for OT-style alarm buses
MQTT 8 fits SCADA-friendly architectures that already publish alarms and statuses on a message bus. It is lightweight and supports retained messages, which helps late subscribers get the latest status fast.
MQTT integration should be designed with security in mind:
- TLS
- Client certificates or strong credentials
- Topic naming standards
- Rate limits to avoid storm events during outages
| Integration method | Best for | Strength | Key requirement |
|---|---|---|---|
| SNMP polling | Trend dashboards | Simple and common | Good OID design and polling rate control |
| SNMP traps | Fast alarms | Low latency | Trap receiver and filtering rules |
| HTTPS webhooks | ITSM and cloud monitoring | Flexible payloads | TLS policy and endpoint allowlist |
| MQTT | OT telemetry and SCADA alarm buses | Lightweight and scalable | Broker security and topic governance |
A practical approach is hybrid. Use SNMP for core NMS visibility. Use traps or MQTT for fast alarms. Use webhooks for incident workflows.
Once health can be seen, the last question is action. A heartbeat alarm should not only “notify.” It should also trigger a safe response path.
What failover actions trigger on heartbeat loss—backup SIP proxy, emergency auto-dial, relay output, or audible alert?
A heartbeat system is only useful when it drives the right action. Actions should match risk level. A short SIP delay should not trigger a siren. A confirmed loss of service in a critical zone should.
On heartbeat loss, the safest failover actions are staged: first switch to a backup SIP proxy, then raise a remote alarm, then trigger local actions like relay output or audible alert. Auto-dial can be used carefully for life-safety scenarios when the plant policy allows it.
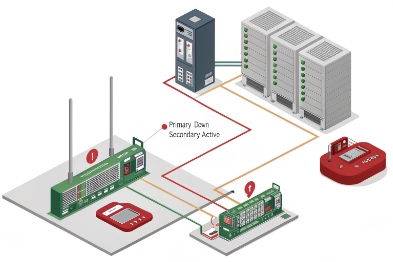
Stage 1: network and SIP recovery
First actions should be quiet and automatic:
- Re-resolve the proxy (DNS SRV records 9 or static secondary).
- Re-register to a backup SIP proxy.
- Restart the SIP stack if the transport session is stuck.
- Rebuild the TLS session if needed.
This stage should not create noise for operators unless it fails.
Stage 2: notify the monitoring system
If recovery fails after a defined time window, send:
- SNMP trap or MQTT event
- Syslog event if the plant uses it
- Dashboard status change
This stage is where the NOC or control room can decide the next step.
Stage 3: local safety actions
Local actions are useful when the phone is in a critical point and people nearby must know it is offline:
- Drive a relay output to light a beacon or activate an input on a PLC.
- Trigger an audible alert on the phone or nearby horn (site-dependent).
- Flash the phone LED if the design supports it.
Local actions should have a latch and a reset method. They should not oscillate during unstable networks.
Stage 4: emergency auto-dial, used with strict rules
Auto-dial on heartbeat loss is powerful and risky. It can create nuisance calls during maintenance. It can also flood an emergency desk. If a site wants auto-dial, it should be gated by conditions like:
- Only after a long confirmed outage
- Only in certain zones
- Only when a local input confirms “critical mode”
- Only once per outage with a cooldown timer
| Trigger condition | Best action | Why this action fits | Guardrail |
|---|---|---|---|
| 1–2 missed OPTIONS | No action, mark degraded | Avoid false alarms | Require multiple misses |
| Confirmed proxy loss, link OK | Switch to backup proxy | Fast recovery | Limit failover frequency |
| Link down or PoE fault | Send alarm, no proxy action | Proxy is not the cause | Use switch PoE alarms |
| Long confirmed service loss | Relay + audible/LED | Local awareness | Latch + manual reset |
| Critical policy, extended outage | Optional auto-dial | Escalation to humans | One-shot + cooldown + maintenance disable |
A staged plan keeps the system calm under normal noise. It also ensures real outages trigger clear, reliable escalation.
Conclusion
Explosion-proof SIP phones can support heartbeat monitoring. A layered keepalive plan, stable alarm timers, strong integration, and staged failover actions reduce downtime and false alarms.
Footnotes
-
SIP OPTIONS A SIP method often used as a heartbeat mechanism to check the availability and capabilities of a SIP user agent or server. ↩
-
TCP keepalive A feature that sends probe packets on an idle TCP connection to verify the peer is still reachable. ↩
-
RTCP RTP Control Protocol, used to monitor data delivery quality in large multicast networks. ↩
-
SIP REGISTER The SIP method used by a user agent to notify a registrar of its current IP address and contact information. ↩
-
STUN Session Traversal Utilities for NAT; a protocol that allows applications to discover the presence and type of NAT and obtain public IP addresses. ↩
-
SNMP Simple Network Management Protocol; a standard for collecting and organizing information about managed devices on IP networks. ↩
-
Webhooks A method for an app to provide other applications with real-time information via HTTP callbacks. ↩
-
MQTT A lightweight messaging protocol for small sensors and mobile devices, optimized for high-latency or unreliable networks. ↩
-
SRV records A DNS record that specifies the hostname and port number of servers for specified services. ↩











